Secure and Effective: Making Best Use Of Cloud Solutions Advantage
In the fast-evolving landscape of cloud services, the junction of protection and effectiveness stands as a crucial time for organizations looking for to harness the full capacity of cloud computer. By thoroughly crafting a framework that focuses on information defense through file encryption and gain access to control, organizations can strengthen their electronic assets versus impending cyber risks. The quest for optimal efficiency does not end there. The equilibrium in between guarding data and ensuring streamlined operations calls for a strategic approach that requires a deeper exploration right into the elaborate layers of cloud solution monitoring.
Information Encryption Finest Practices
When carrying out cloud solutions, utilizing robust information security best techniques is vital to guard sensitive info efficiently. Information encryption includes inscribing information in such a method that only authorized celebrations can access it, making certain privacy and safety. One of the essential ideal practices is to make use of strong security algorithms, such as AES (Advanced Encryption Requirement) with tricks of adequate length to shield data both en route and at remainder.
Furthermore, implementing appropriate essential monitoring techniques is vital to maintain the safety of encrypted data. This consists of firmly producing, storing, and rotating security tricks to avoid unauthorized accessibility. It is likewise essential to secure information not only throughout storage yet also during transmission between users and the cloud company to protect against interception by destructive stars.
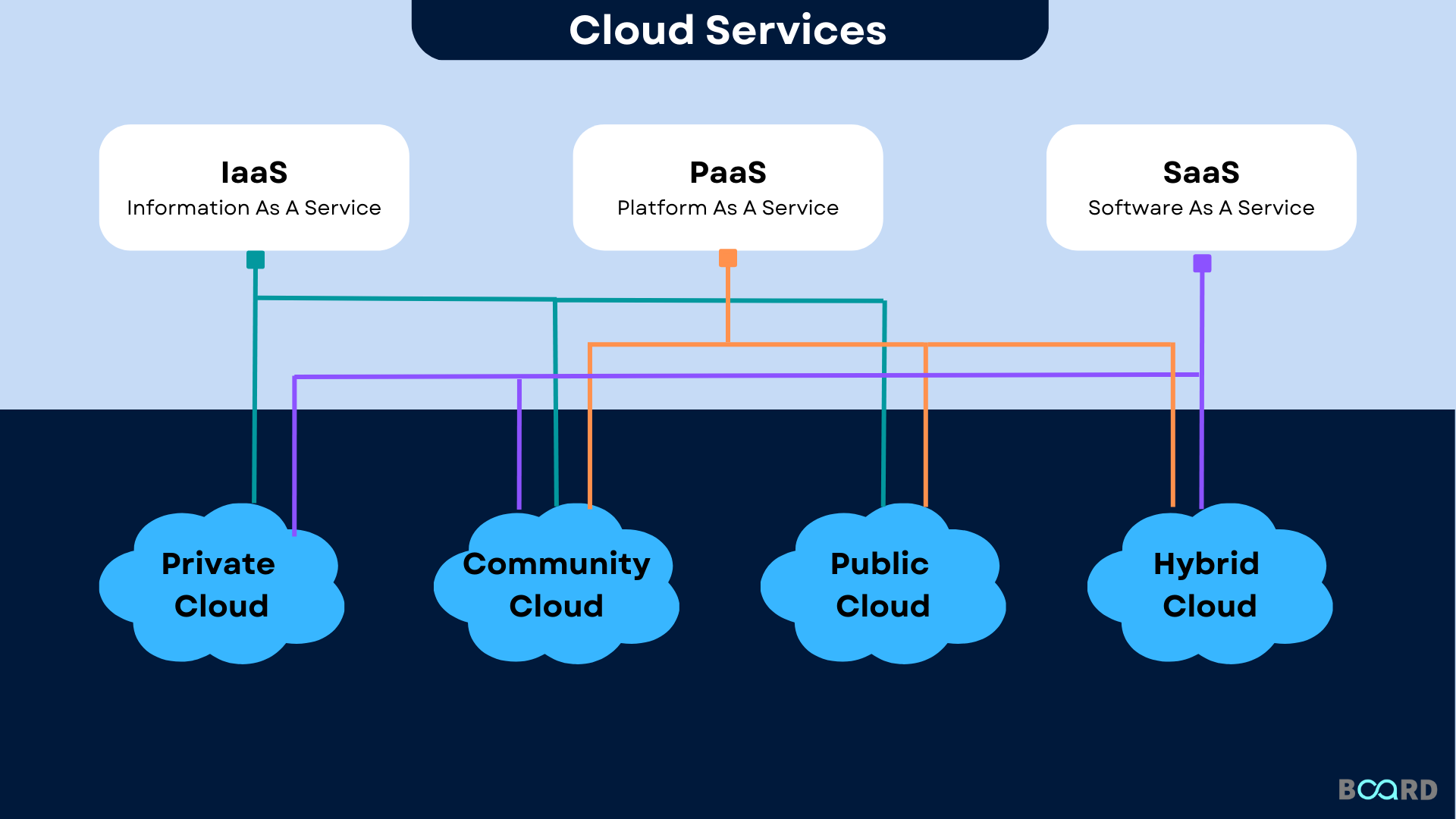
Source Allotment Optimization
To make best use of the benefits of cloud solutions, organizations have to concentrate on maximizing source allowance for effective operations and cost-effectiveness. Resource allocation optimization entails purposefully dispersing computer resources such as processing storage space, network, and power data transfer to meet the differing demands of workloads and applications. By executing automated source allowance systems, organizations can dynamically readjust source circulation based upon real-time demands, guaranteeing optimum efficiency without unneeded under or over-provisioning.
Effective source allocation optimization leads to enhanced scalability, as resources can be scaled up or down based on use patterns, causing boosted versatility and responsiveness to altering company requirements. Moreover, by properly lining up sources with work demands, organizations can lower functional expenses by getting rid of wastage and making the most of utilization efficiency. This optimization likewise boosts general system reliability and durability by avoiding source bottlenecks and making sure that vital applications obtain the needed resources to operate smoothly. To conclude, source allowance optimization is important for companies seeking to leverage cloud solutions effectively and securely.
Multi-factor Verification Implementation
Carrying out multi-factor verification improves the protection position of companies by requiring extra verification steps past just a password. This included layer of security substantially reduces the risk of unauthorized accessibility to delicate information and systems. Multi-factor authentication generally integrates something the individual recognizes (like a password) with something they have (such as a smart phone) or something they are (like a finger print) By incorporating multiple aspects, the likelihood of a cybercriminal bypassing the authentication procedure is substantially diminished.
Organizations can select from different techniques of multi-factor authentication, consisting of text codes, biometric scans, hardware symbols, or authentication apps. Each method offers its own degree of protection and ease, permitting businesses to select the most suitable option based on their unique needs and resources.
Additionally, multi-factor verification is critical in securing remote accessibility to shadow services. With the boosting fad of remote work, ensuring that just authorized workers can access critical systems and data is vital. By implementing multi-factor authentication, companies can strengthen their defenses against potential safety violations and information burglary.
Disaster Recovery Planning Techniques
In today's digital landscape, efficient calamity recovery planning methods are essential for organizations to alleviate the influence of unexpected interruptions on their data and operations honesty. A durable calamity recuperation strategy requires identifying prospective dangers, analyzing their possible impact, and executing positive procedures to make certain business connection. One crucial facet of disaster recovery planning is producing backups of vital information and systems, both on-site and in the cloud, to make it possible for speedy reconstruction in instance of an incident.
Moreover, organizations should conduct universal cloud Service routine testing and simulations of their disaster healing procedures to identify any kind of weaknesses and improve response times. It is likewise vital to develop clear interaction procedures and assign accountable individuals or teams to lead recuperation initiatives throughout a dilemma. Furthermore, leveraging cloud services for disaster recuperation can give cost-efficiency, scalability, and flexibility compared to typical on-premises services. By focusing on calamity recovery preparation, organizations can minimize downtime, shield their track record, and preserve operational strength when faced with unexpected events.
Performance Keeping Track Of Devices
Efficiency monitoring tools play a critical function in providing real-time insights right into the wellness and performance of a company's systems and applications. These tools make it possible for businesses to track numerous efficiency metrics, such as action times, resource application, and throughput, allowing them to recognize bottlenecks or prospective concerns proactively. By continually checking key efficiency indicators, companies can ensure optimal performance, determine fads, and make informed decisions to boost their general functional performance.
One prominent efficiency surveillance tool is Nagios, understood for its capability to check solutions, web servers, and networks. It offers detailed surveillance and alerting services, guaranteeing that any type of inconsistencies from established performance thresholds are quickly determined and attended to. An additional extensively used tool is Zabbix, providing tracking abilities for networks, servers, online makers, and cloud solutions. Zabbix's straightforward user interface and personalized attributes make it a beneficial asset for companies seeking durable efficiency monitoring remedies.
Verdict
In the fast-evolving landscape of cloud services, the intersection of protection and effectiveness stands as a crucial time for companies seeking to harness the complete possibility of cloud computer. The balance between guarding data and making sure structured procedures requires a strategic approach that necessitates a deeper exploration into the intricate layers of cloud service monitoring.
When carrying out cloud solutions, employing robust information encryption finest techniques is critical to protect delicate information effectively.To maximize the advantages of cloud solutions, companies must concentrate on enhancing source appropriation for efficient operations and cost-effectiveness - linkdaddy cloud services press release. In conclusion, resource appropriation optimization is important for companies looking to utilize cloud services successfully and safely